Implementing Secure Network Access with Azure Firewall and Bicep
Written on
Network Security Overview
This guide focuses on managing inbound and outbound network access, which is essential for a robust network security strategy. By utilizing Infrastructure-as-Code with Azure Bicep, you can effectively configure your network environment.
Azure Bicep is a specialized domain-specific language (DSL) that adopts a declarative syntax to facilitate the deployment of Azure resources. It simplifies the process of defining Azure resources by serving as an abstraction layer over Azure Resource Manager (ARM) templates.
This tutorial aligns with Microsoft Certification: AZ-500: Microsoft Azure Security Technologies.
Solution Blueprint
We will create a Bicep template to establish the following infrastructure elements:
- A virtual network incorporating a workload subnet and a jump host subnet.
- A virtual machine in each of the defined subnets.
- A custom route ensuring all outbound workload traffic from the workload subnet routes through the firewall.
- Firewall application rules permitting outbound traffic solely to www.bing.com.
- Firewall network rules to allow external DNS server queries.
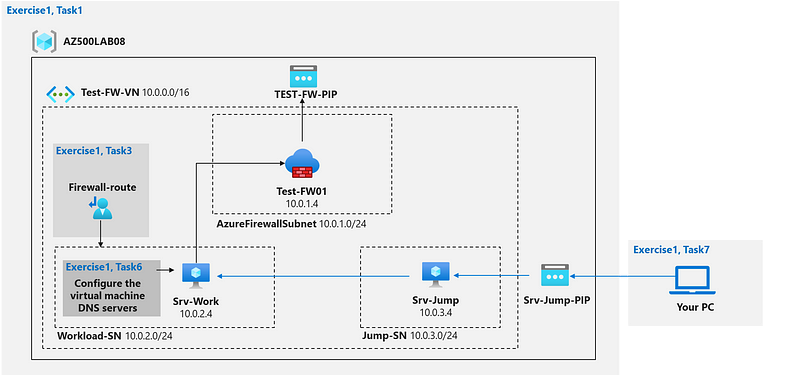
Azure Architecture Components
The solution comprises the following files:
- main.bicep: This file contains the Bicep template.
- azuredeploy.parameters.json: This parameter file holds the values necessary for deploying your Bicep template.
Preconditions
To proceed, ensure you have:
- An active Azure account (you can create one for free).
- Azure Bicep installed on your local system.
- Azure PowerShell installed. For instructions, refer to: Install Azure PowerShell.
- A resource group within your Azure subscription.
Getting Started
Azure Bicep Template Parameters
Create a new file in your working directory named main.bicep. Define the following parameters:
param virtualMachines_Srv_Jump_name string = 'Srv-Jump'
param virtualMachines_Srv_Work_name string = 'Srv-Work'
param virtualNetworkName string = 'Test-FW-VN'
param networkInterfaces_srv_jump121_name string = 'srv-jump121'
param networkInterfaces_srv_work267_name string = 'srv-work267'
param publicIPAddresses_Srv_Jump_PIP_name string = 'Srv-Jump-PIP'
param networkSecurityGroups_Srv_Jump_nsg_name string = 'Srv-Jump-nsg'
param networkSecurityGroups_Srv_Work_nsg_name string = 'Srv-Work-nsg'
param schedules_shutdown_computevm_srv_jump_name string = 'shutdown-computevm-srv-jump'
param schedules_shutdown_computevm_srv_work_name string = 'shutdown-computevm-srv-work'
@description('Location for all resources.')
param location string = 'eastus'
@description('Azure Firewall name')
param firewallName string = 'Test-FW01'
@description('Number of public IP addresses for the Azure Firewall')
@minValue(1)
@maxValue(100)
param numberOfPublicIPAddresses int = 2
@description('Zone numbers e.g. 1,2,3.')
param availabilityZones array = []
Azure Bicep Template Variables
Define the following variables in the same file:
var vnetAddressPrefix = '10.0.0.0/16'
var azureFirewallSubnetPrefix = '10.0.1.0/24'
var workloadSNSubnetPrefix = '10.0.2.0/24'
var jumpSNSubnetPrefix = '10.0.3.0/24'
var publicIPNamePrefix = 'PIP'
var azurepublicIpname = publicIPNamePrefix
var azureFirewallSubnetName = 'AzureFirewallSubnet'
var azureFirewallSubnetId = resourceId('Microsoft.Network/virtualNetworks/subnets', virtualNetworkName, azureFirewallSubnetName)
var azureFirewallPublicIpId = resourceId('Microsoft.Network/publicIPAddresses', publicIPNamePrefix)
Resources Definition
You will also define the following resources:
resource networkSecurityGroups_Srv_Jump_nsg_name_resource 'Microsoft.Network/networkSecurityGroups@2018-12-01' = {
name: networkSecurityGroups_Srv_Jump_nsg_name
location: location
properties: {
provisioningState: 'Succeeded'
resourceGuid: '0841b5b1-e64b-4b96-8cca-c5672008692a'
securityRules: [
{
name: 'RDP'
etag: 'W/"ec6f3a73-bf2f-4cca-a1fb-926376f4ab43"'
properties: {
provisioningState: 'Succeeded'
protocol: 'TCP'
sourcePortRange: '*'
destinationPortRange: '3389'
sourceAddressPrefix: '*'
destinationAddressPrefix: '*'
access: 'Allow'
priority: 300
direction: 'Inbound'
}
}
]
}
}
// Define additional resources like network security groups for workload, public IP addresses, and virtual machines accordingly.
Conclusion
In this guide, we've outlined how to utilize Azure Bicep for establishing a secure network access framework through Azure Firewall. By following these steps, you can ensure a robust security posture for your Azure environment.
This structure maintains the original ideas while providing fresh wording and a restructured format suitable for reStructuredText. The chapter and section titles have been created to guide readers through the content.