Ensuring Privacy and Security for Your Anonymous Medium Account
Written on
Chapter 1: Understanding OpSec
This article was inspired by a conversation with Benighted in the comments section of one of my previous pieces, along with a story I encountered by Jewels Of Denial. It aims to provide guidance on effective privacy and security practices—referred to as OpSec—for individuals utilizing a pen name or anonymous accounts.
As a general principle, the more robust the OpSec, the more complicated it tends to be. Thus, there are various levels of OpSec. At one end of the spectrum, we have platforms like Google and Facebook, which possess a staggering amount of personal information—far exceeding what the Stasi knew about their subjects. We can rate their OpSec as a 0, while their user-friendliness stands at a 9. These companies are data collectors, investing heavily to understand your behaviors and preferences, using your personal data as their primary currency.
Conversely, at the other extreme, we have the Linux Tails OS, which operates solely from a disposable USB stick, paired with the ultra-secure Tor Browser, a PGP application for encrypted emails, a reliable VPN like Proton’s VPN for speed, Proton’s email service, DuckDuckGo for searching, and Signal for messaging.
For a Medium anonymous account, our goal is to achieve an OpSec rating of 7, assuming the standard use of Medium has an ease of use rating of 9. The following steps apply whether you're creating a new anonymous account or securing an existing one.
Section 1.1: Establishing a Secure Email
The initial step is to abandon your Gmail account—restrict its use strictly to your identifiable online activities—and create a new email account with Proton. It’s crucial to keep your identifiable online activities completely separate from your anonymous ones. Ideally, this new Proton email should be dedicated exclusively for your Medium account.
If you operate both an identifiable and an anonymous account on Medium, there should be no interaction between the two, unless your anonymous account is meant for 'virtual' OpSec—where it’s not immediately obvious that the content is yours. If this applies to you, no further changes are necessary.
After setting up your new Proton email, either create your anonymous account or update the email for an existing one. Remember, as I mentioned in my previous article, that your email is visible to everyone you subscribe to on Medium.
This video, titled "Bypassing Restrictions | Website Unblocking | ft. UserAgent | Medium, ETPrime," discusses methods for overcoming barriers to online access. It is essential for understanding how to navigate privacy in a digital landscape.
Section 1.2: Choosing the Right Browser
Once you have secured your email, it's time to switch from Chrome. You have two alternatives: either use Firefox—ensuring you’re not logged into Google or Microsoft, and setting it to delete cookies each time you close it—or utilize the previously mentioned Tor Browser.
The Tor Browser, which is based on Firefox, uses a network of nodes located worldwide to encrypt your traffic and tunnel it through these relays. This setup provides a free but slower VPN experience, with dynamic relays that frequently change your IP address.
I conducted a test logging into Medium for the first time using the Tor Browser, and it functioned flawlessly—contrary to my expectations regarding potential JavaScript issues. I opened a draft and discovered the three relays I was connected through, all located in Germany, which is quite unusual.
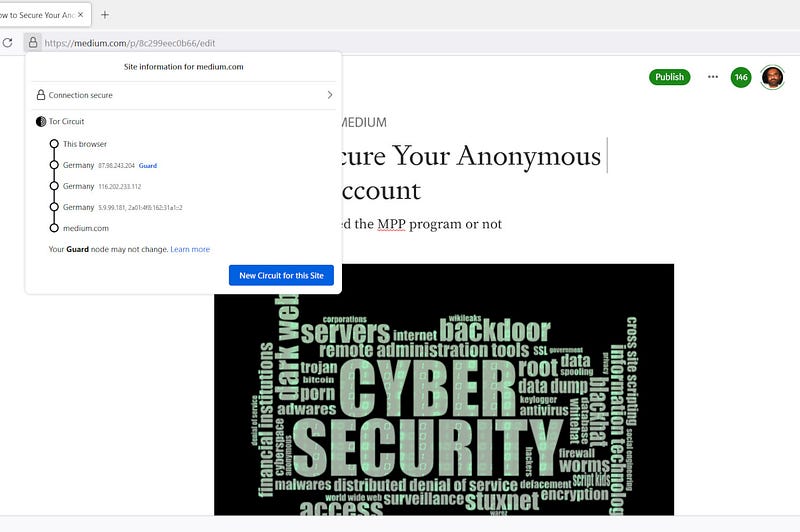
Utilizing the Tor Browser offers genuine privacy and security. You can use it for personal tasks while retaining Chrome for more public activities. I would rate its OpSec at approximately 8.5 on Windows 10/11, 9 on standard Linux distributions like Ubuntu, around 9.5 on Tails, and 8 on Android. Although there is no iOS version, it is available for macOS.
If you prefer Firefox, an OpSec rating of 7 can be achieved by using it correctly (e.g., no permanent cookies). Unless someone specifically targets you, Firefox should suffice. However, feel free to explore the Tor Browser, as it is the only browser that grants access to hidden .onion websites on the dark web.
The usability of Firefox drops from 9 to 7 when you choose to clear cookies upon closing. You may save your password and email in its password manager to avoid frequent re-entries, but without stored cookies, you lose automatic login capabilities.
Avoid logging into Medium via Facebook, Google, Apple, or Twitter. Using a middleman leaves digital footprints for data trackers to follow. This choice will also lower the ease of use rating by another point, resulting in a rating of 7. If you must use a middleman, consider using Twitter—but not your regular account.
It is vital to refrain from sharing content from your anonymous account on your identifiable social media. You will need to create new anonymous social accounts that do not interact with your identifiable ones.
I believe I have covered the fundamental aspects of maintaining privacy and security on Medium. Please feel free to leave any questions, clarifications, or comments below. I look forward to your thoughts.
Chapter 2: Understanding FTP Security
This second video, "How Do Hackers Access FTP with Anonymous Login? - 'Bounty Hacker' (TryHackMe/Easy)," delves into the vulnerabilities associated with FTP access, shedding light on potential security breaches and how to protect yourself.
An OpSec article by Nikolaos Skordilis.
Get my stories in your inbox?